MoTB #13: Reflected XSS in Brightkite
What is Brightkite
"Brightkite is a location-based social network. In real time you can see where your friends are and what they're up to. Depending on your privacy settings you can also meet others nearby." (Brightkite home page)
Twitter effect
Brightkite can be used to send new tweets and reply to other Twitter users.
Brightkite is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
16th place in the most used twitter clients, according to “TwitStats” - 4 twits




Vulnerability: Reflected Cross-Site in the "Person not found" page.
Status: Patched.
Details: The Brightkite "Person not found" page did not encode HTML entities in the people query variable, which could have allowed the injection of scripts.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
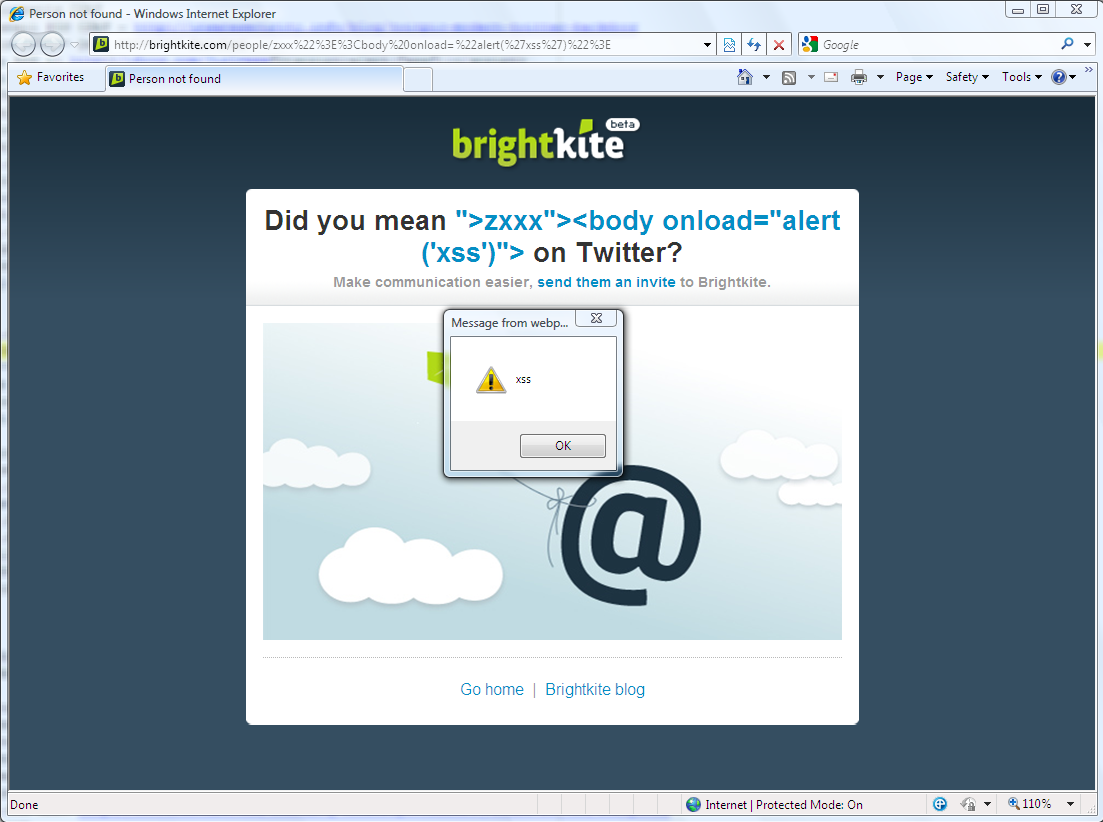
Proof-of-Concept: http://brightkite.com/people/zxxx%22%3E%3Cbody%20onload=%22alert(%27xss%27)%22%3E
Screenshot:
Vendor response rate
Vulnerability was fixed 1 hour after it has been reported. Excellent - 5 twits.





"Brightkite is a location-based social network. In real time you can see where your friends are and what they're up to. Depending on your privacy settings you can also meet others nearby." (Brightkite home page)
Twitter effect
Brightkite can be used to send new tweets and reply to other Twitter users.
Brightkite is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
16th place in the most used twitter clients, according to “TwitStats” - 4 twits




Vulnerability: Reflected Cross-Site in the "Person not found" page.
Status: Patched.
Details: The Brightkite "Person not found" page did not encode HTML entities in the people query variable, which could have allowed the injection of scripts.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
Proof-of-Concept: http://brightkite.com/people/zxxx%22%3E%3Cbody%20onload=%22alert(%27xss%27)%22%3E
Screenshot:

Vendor response rate
Vulnerability was fixed 1 hour after it has been reported. Excellent - 5 twits.






2 Comments:
same here:)
http://brightkite.com/wall?identifier="XSS"
http://i26.tinypic.com/2vmczv8.jpg
d3v1l, we fixed that this morning. Thanks for pointing it out. :)
Lesley Yarbrough
Community Manager
Brightkite.com
Post a Comment
<< Home