MoTB #14: Reflected XSS in TweetMeme
What is TweetMeme
"TweetMeme is a service which aggregates all the popular links on twitter to determine which links are popular. TweetMeme is able to categorize these links into categories and subcategories, making it easy to filter out the noise to find what your interested in." (TweetMeme about page)
Twitter effect
TweetMeme can be used to send new tweets and reply to other Twitter users.
TweetMeme is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
6.5 Million unique visitors per month (According to Compete) - 4.5 twits





Vulnerability: Reflected Cross-Site in the Search page.
Status: Patched.
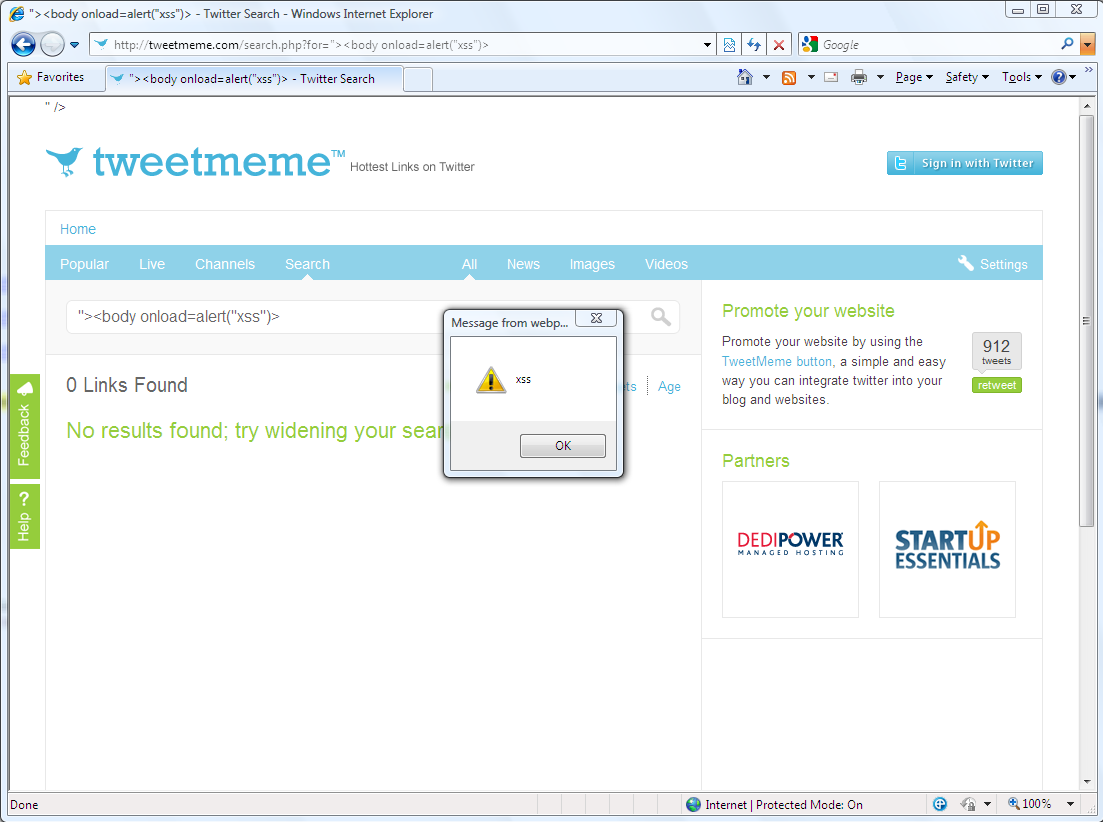
Details: The TweetMeme search page did not encode HTML entities in the "for" variable, which could have allowed the injection of scripts.
The vulnerability was also submitted, and publicly disclosed by d3v1l.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
Proof-of-Concept: http://tweetmeme.com/search.php?for=%3C/title%3E%3Cscript%3Ealert(%22xss%22);%3C/script%3E%3Ctitle%3E
Screenshot:
Vendor response rate
Vulnerability was fixed 2 hours after it has been reported. Excellent - 5 twits.





"TweetMeme is a service which aggregates all the popular links on twitter to determine which links are popular. TweetMeme is able to categorize these links into categories and subcategories, making it easy to filter out the noise to find what your interested in." (TweetMeme about page)
Twitter effect
TweetMeme can be used to send new tweets and reply to other Twitter users.
TweetMeme is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
6.5 Million unique visitors per month (According to Compete) - 4.5 twits





Vulnerability: Reflected Cross-Site in the Search page.
Status: Patched.
Details: The TweetMeme search page did not encode HTML entities in the "for" variable, which could have allowed the injection of scripts.
The vulnerability was also submitted, and publicly disclosed by d3v1l.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
Proof-of-Concept: http://tweetmeme.com/search.php?for=%3C/title%3E%3Cscript%3Ealert(%22xss%22);%3C/script%3E%3Ctitle%3E
Screenshot:

Vendor response rate
Vulnerability was fixed 2 hours after it has been reported. Excellent - 5 twits.






1 Comments:
Would you mind telling me what exactly you mean by ENCODE, to fix issues like this.
"did not encode HTML entities"
you mean using the php function htmlentities?
I wrote my own small twitter api app, although it is private it would still be nice to know I did it correctly.
Thanks.
Post a Comment
<< Home