MoTB #10: CSRF+XSS vulnerabilities in Twitiq
What is Twitiq
"TwitIQ is an enhanced Twitter interface that provides insight into your Twitter stream and Twitter followers." (Twitiq home page)
Twitter effect
Twitiq can be used to send tweets, direct messages and follow/unfollow other Twitter users.
Twitiq is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
A new 3rd party service, which already gained 5K unique visitors per month (according to Compete)- 1 twit

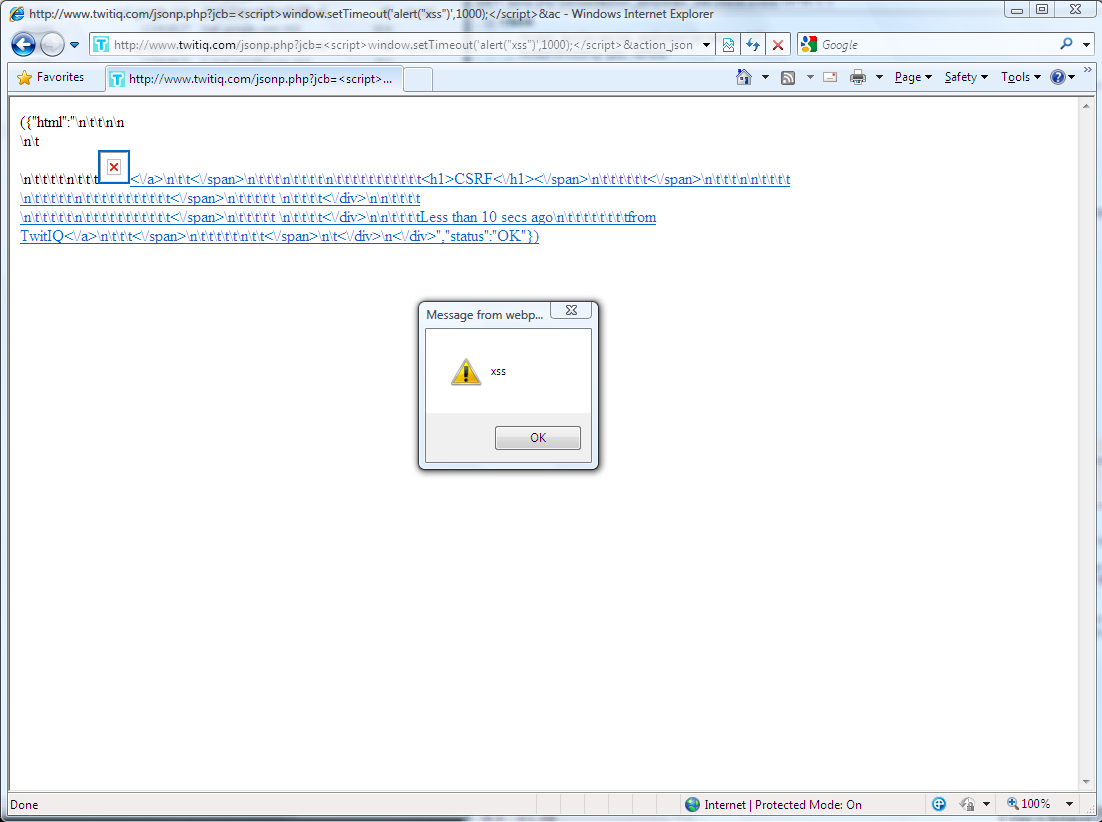
Vulnerability: Cross-Site Request Forgery and Cross-Site Scripting in jsonp.php.
Status: Patched.
Details: The Twitiq jsonp.php web page did not use authenticity code in order to validate that the HTTP post is coming from the Twitiq web application. Also, the jsonp.php did not encode HTML entities in the "jcb" variable.
Both vulnerabilities could have been used by an attacker to automatically send tweets, direct messages or follow/unfollow other twitter users on behalf of it's victims.
Proof of Concept: http://www.twitiq.com/jsonp.php?jcb=%3Cscript%3Ealert("xss")%3C%2Fscript%3E&action_jsonp=new_status&status=CSRF
Screenshots:
Vendor response rate
The vulnerabilities were fixed within 1 hour after they have been reported. Excellent - 5 twits.





"TwitIQ is an enhanced Twitter interface that provides insight into your Twitter stream and Twitter followers." (Twitiq home page)
Twitter effect
Twitiq can be used to send tweets, direct messages and follow/unfollow other Twitter users.
Twitiq is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
A new 3rd party service, which already gained 5K unique visitors per month (according to Compete)- 1 twit

Vulnerability: Cross-Site Request Forgery and Cross-Site Scripting in jsonp.php.
Status: Patched.
Details: The Twitiq jsonp.php web page did not use authenticity code in order to validate that the HTTP post is coming from the Twitiq web application. Also, the jsonp.php did not encode HTML entities in the "jcb" variable.
Both vulnerabilities could have been used by an attacker to automatically send tweets, direct messages or follow/unfollow other twitter users on behalf of it's victims.
Proof of Concept: http://www.twitiq.com/jsonp.php?jcb=%3Cscript%3Ealert("xss")%3C%2Fscript%3E&action_jsonp=new_status&status=CSRF
Screenshots:

Vendor response rate
The vulnerabilities were fixed within 1 hour after they have been reported. Excellent - 5 twits.





