MoTB #30: TweetDeck Insecure Communication Vulnerability
"TweetDeck is your personal browser for staying in touch with what’s happening now, connecting you with your contacts across Twitter, Facebook and more. TweetDeck shows you everything you want to see at once, so you can stay organised and up to date." (TweetDeck about page)
Twitter effect
TweetDeck can be used to send tweets, direct messages and follow/unfollow other Twitter users from multiple Twitter accounts.
TweetDeck is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
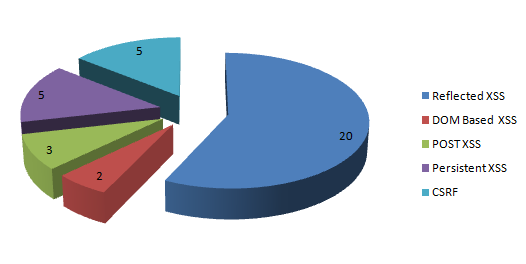
The most popular Twitter clients. 2nd place in the most used twitter clients, with 25.6% usage in the past week - 5 twits





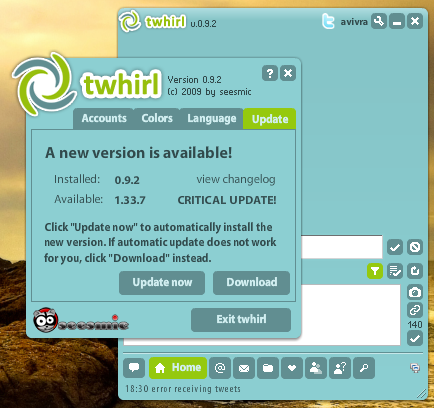
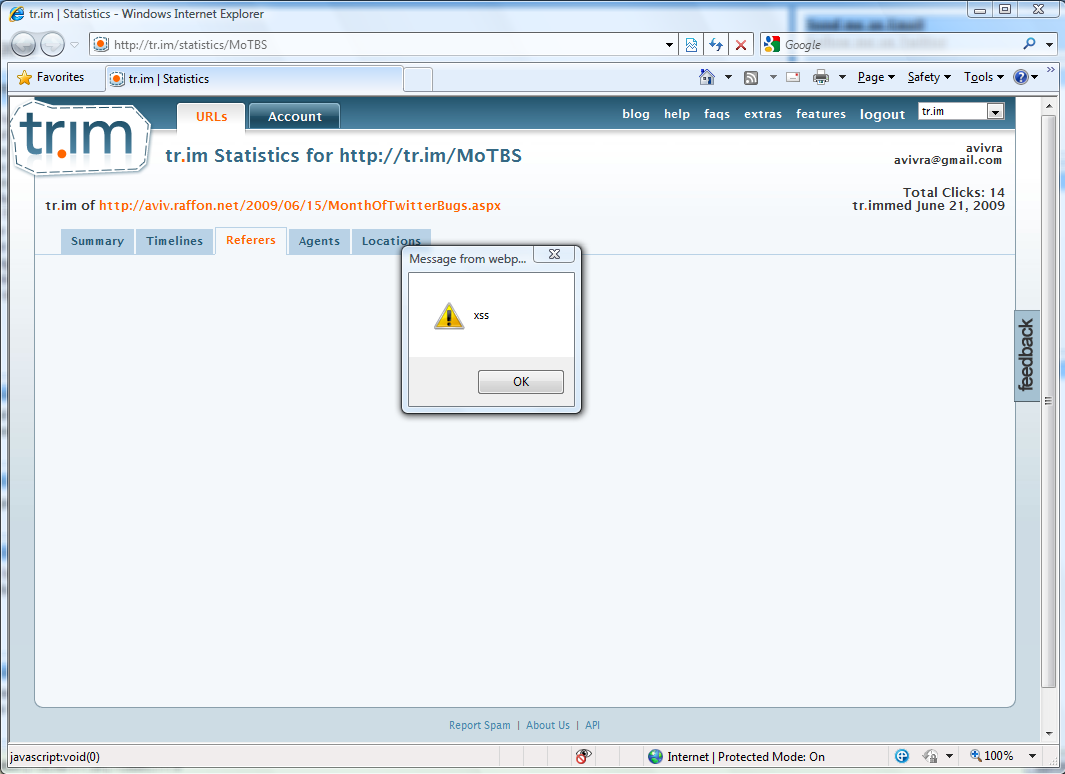
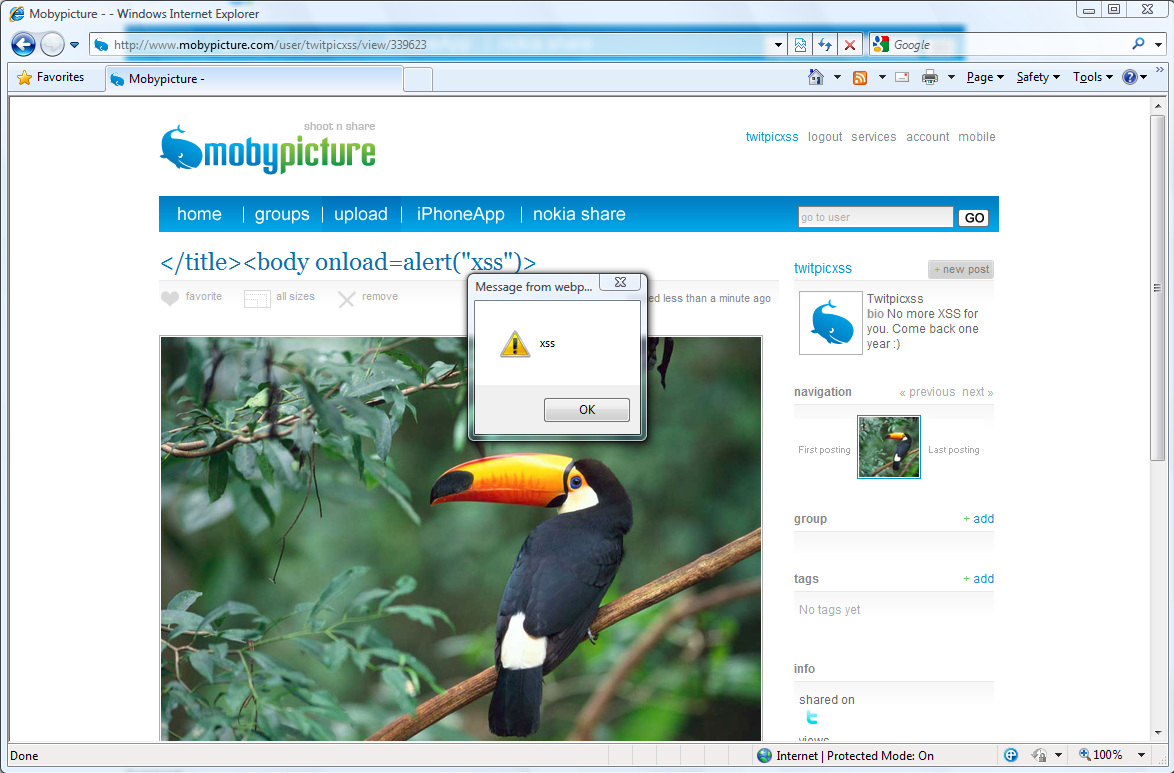
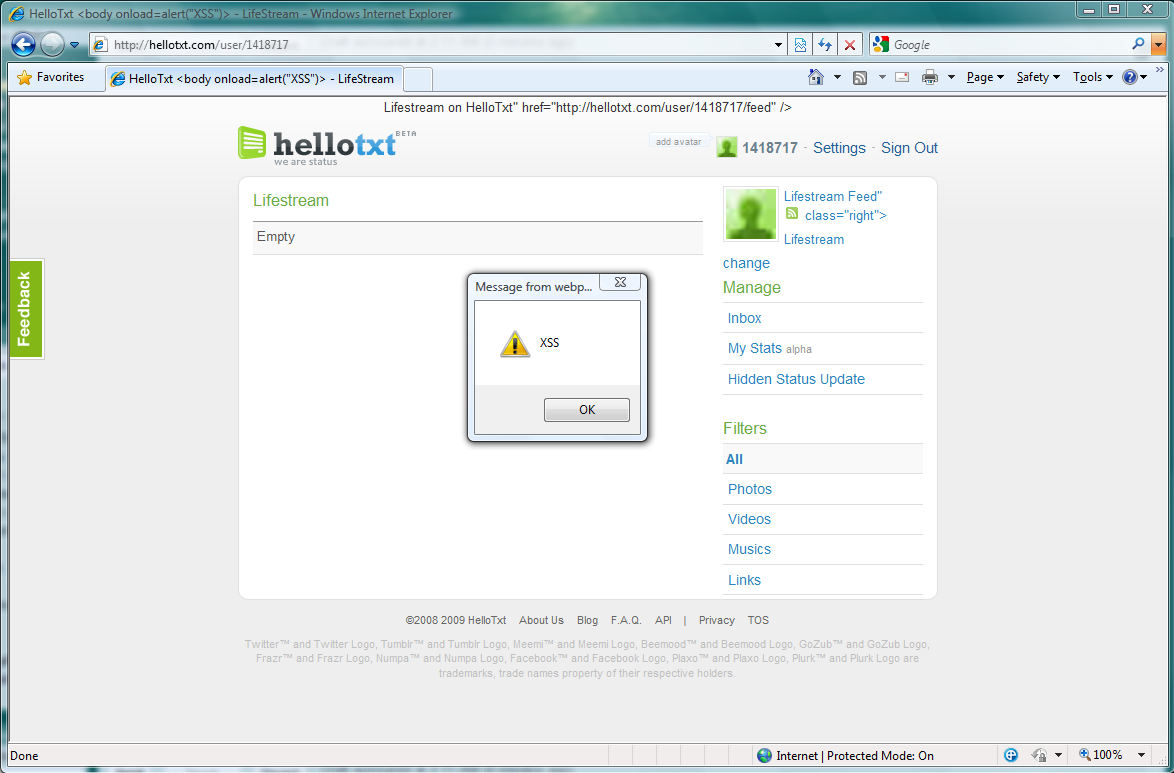
Vulnerability: Insecure communication vulnerability when displaying videos.
Status: Unpatched.
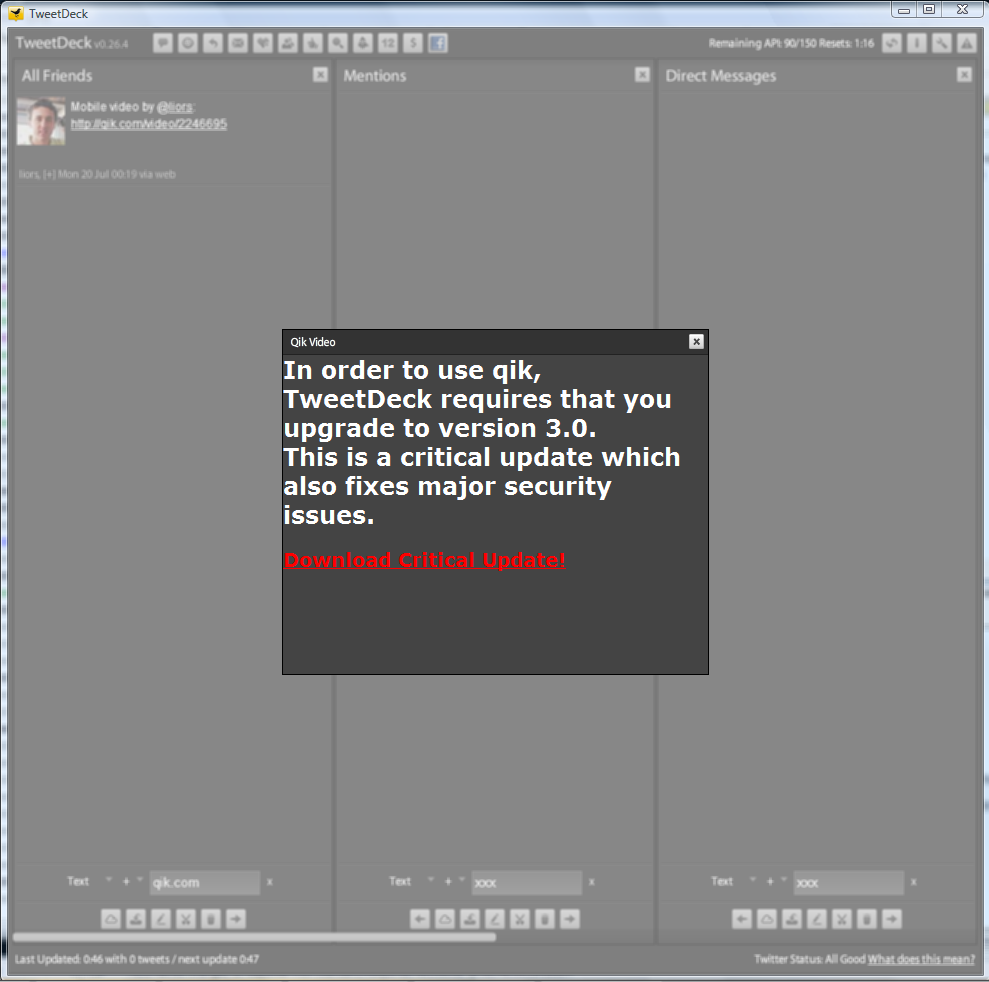
Details: TweetDeck does not use a secure communication when it displays videos inline (e.g. using Qik). An attacker who controls the victim's network (e.g. via public WiFi, compromised DNS servers, etc.) can tamper with the request to the video website and replace it with a rogue content (e.g. display a fake malicious update request).
This vulnerability can be used by an attacker to install malware on its victims machines.
Screenshot:
Vendor response rate
The vendor has confirmed this as a vulnerability. They are working with their partners (Qik and 12seconds) in order to replace the current HTTP connection with HTTPS. While the vendor have yet to fix the vulnerability, they were very responsive and have promised to release a patch as soon as their partners will implement SSL on their websites. Almost Good - 3.5 twits.